October marks Cybersecurity Awareness Month, and this year’s theme, Building a Cyber-Strong America, focuses on strengthening awareness at every level, from individuals to national defense.
At its core, cybersecurity is about readiness: knowing what’s happening, where it’s happening, and how to respond. That kind of readiness starts with visibility. Understanding how threats change over time, how fast they spread, and how one event can ripple into another.
To help bring that picture into focus, our team created a new Cyber Intelligence Dashboard and StoryMap. The Dashboard brings together cyberattack behaviors, targeting patterns, and real-time reports of malicious IPs, giving analysts a single view of what’s unfolding around the world. The StoryMap builds on that foundation, connecting major cyber incidents over the years to show how they’ve shaped the risks we see today.
This month’s issue takes a closer look at both tools and how they fit into the bigger picture of digital defense. We’ll also explore how Artificial Intelligence (AI) is changing the fight. from long-standing automation to the rise of agentic AI, and how both attackers and defenders are adapting to stay ahead.
The Cyber Intelligence Dashboard
Our Cyber Intelligence Dashboard provides two complementary views of global threat activity.
The Crowd-Sourced IPs tab compiles a verified static snapshot of reported malicious IPs. It gives analysts a reference point to identify known bad actors, review behavior patterns, and compare them against live reports.
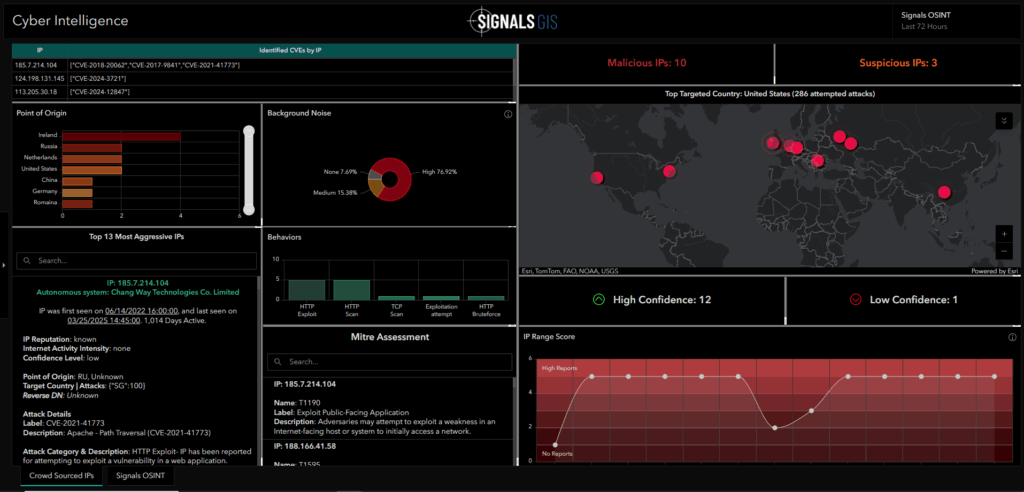
The Signals OSINT tab focuses on open-source threat reporting. It aggregates posts from media feeds, maps the geographic spread of reports, and applies sentiment and similarity analysis to highlight trending cyber events.
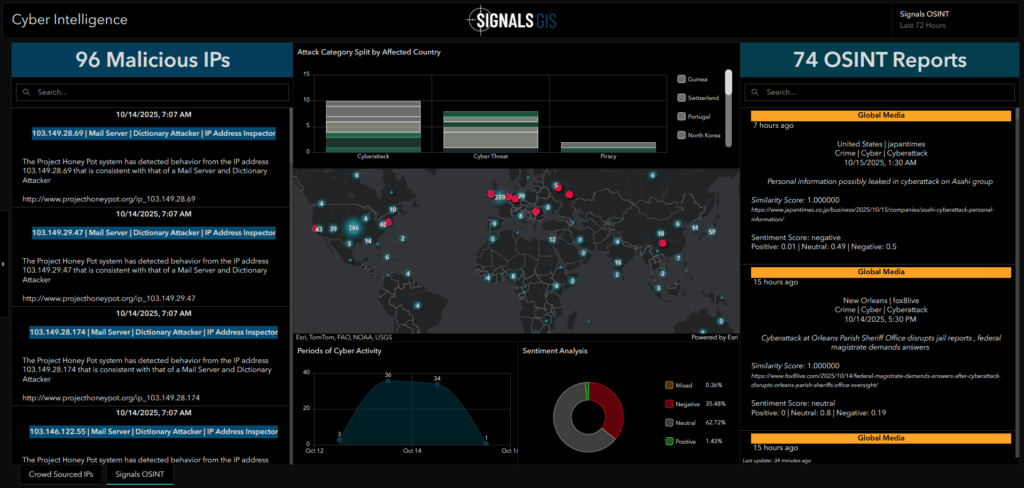
Together, these tabs connect technical indicators with real-world reporting. By combining structured IP data with human-generated intelligence, the dashboard helps analysts spot patterns faster, prioritize emerging risks, and understand where activity is most concentrated.
The Storymap
The StoryMap looks back at major cyberattacks from the past three decades, showing how earlier incidents shaped the threats we face today.. It highlights patterns in ransomware, phishing, and large-scale breaches, helping readers understand how modern risks evolved and why awareness remains essential.
AI in Cybersecurity: The Now
AI and automated reasoning have been part of cybersecurity for decades. In the 1980s and 1990s, many intrusion detection systems used expert systems or rule-based logic, where analysts encoded “if-then” rules (for example, if traffic spikes from one source, flag it) to identify suspicious behavior. While these systems didn’t learn or adapt in the modern sense, they automated parts of human analysis by applying defined logic to detect known threats.
Over time, as networks grew and data volumes exploded, the field shifted toward machine learning (ML) algorithms that recognize patterns and anomalies beyond rigid rules. This type of AI learns from data rather than relying solely on static logic, helping detect previously unseen attacks.
Today, attackers use both ML-based and generative AI tools to:
- Craft more convincing phishing campaigns (it is estimated that nearly 80% are now AI-assisted).
- Generate malware that adapts to evade detection.
- Automate reconnaissance and vulnerability scanning.
Defenders, meanwhile, use AI to analyze large volumes of data, identify anomalies, and prioritize potential threats. It assists with alert management, pattern recognition, and simulation training that mirrors real-world attack behavior.
Even as AI reshapes how attacks unfold, there are practical ways to stay secure. Verify unexpected emails or messages before responding, use strong and unique passwords, enable multi-factor authentication wherever possible, and keep systems and software up to date. Staying alert to how AI is being used in phishing and social engineering can make all the difference. Awareness and small, consistent actions are still the strongest defense.
Takeaway: What started as rule logic evolved into machine learning, and now generative AI is expanding what both attackers and defenders can do. Understanding that progression helps us see where AI in cybersecurity stands today, and where it’s headed next.
Agentic AI : The Next Frontier
Agentic AI refers to systems that can plan, make decisions, and adapt their actions based on outcomes. They learn and improve as they go, instead of waiting for a human prompt. It’s a step beyond traditional automation, designed to think through tasks rather than simply execute instructions.
We can already see early versions of this in AI scheduling assistants like Microsoft 365 Copilot and Google Duet. These tools can check calendars, find open slots, and even reschedule meetings automatically if there are meeting conflicts. A small but clear example of AI handling decisions on its own.
In cybersecurity, the implications are far greater. Earlier this year, Palo Alto Networks’ Unit 42 demonstrated an experimental Agentic AI Attack Framework that could complete a full ransomware operation. It executed compromise to data exfiltration in just 25 minutes, roughly 100 times faster than traditional human driven attacks. Their research showed how autonomous AI agents could adapt tactics mid-attack, learn from failed attempts, and chain together multiple stages of the cyber kill chain without human input.
Microsoft is taking the same concept in a defensive direction. In its September 2025 announcement, Microsoft introduced agentic AI capabilities in Sentinel and Security Copilot, describing them as part of a unified agentic platform for defenders. Sentinel’s new graph-based architecture and Model Context Protocol (MCP) server allow AI agents to reason over data, correlate alerts, and take guided actions in real time, all while keeping human analysts in control.
While these advancements present new challenges, they also point to where cyber defense is headed: systems that detect, sort through alerts, prioritize risks, and respond with context and precision. The goal isn’t to replace analysts, but to give them intelligent tools that act faster than attackers can.
As these systems grow more capable, awareness and accountability become even more important. Building a cyber-strong America means understanding not just what AI can do, but how to use it responsibly to strengthen defense, not amplify risk.
Takeaway: Agentic AI is still emerging, but it marks the next shift in how cyber defense tools may operate faster, smarter, and more independently, provided the right safeguards stay in place.
Shared Responsibility in Cyber Defense
For defense contractors and mission partners, these trends have direct implications. As AI accelerates both the speed and scale of cyber threats, safeguarding sensitive data, supply chains, and communication systems becomes even more critical. Strengthening cyber hygiene, maintaining compliance with frameworks like CMMC, and building awareness across the workforce are practical ways to contribute to a stronger, safer defense community.
Building a cyber-strong America starts with awareness. It means understanding the risks, using the tools we have wisely, and recognizing the responsibility we all share in staying prepared. Technology alone isn’t the answer. People still play the biggest role in cybersecurity, with human error behind most data breaches each year. How we interpret information, question what we see, and respond under pressure, matters just as much as the systems themselves.
The threats will keep changing, but the goal remains the same: improve visibility, strengthen defenses, and make informed decisions at every level.